Sybil attack bitcoin mineral

Lecture Notes in Computer Science. Identity-based validation techniques generally provide accountability at the expense of anonymitywhich can be an undesirable tradeoff especially in online forums that wish to permit censorship -free information exchange and open discussion of sensitive topics. The vulnerability of blockchains has been a hot topic in the cryptocurrency community recently, especially after the 51 percent attacks on two proof-of-work cryptocurrencies, Electroneum and Verge. More than one identity can correspond to a sybil attack bitcoin mineral entity.
They are not making a general statement of when it sybil attack bitcoin mineral no longer profitable for anyone else. Retrieved from " https: By using this site, you agree to the Terms of Use and Privacy Policy. Please help to improve this article by introducing more precise citations.
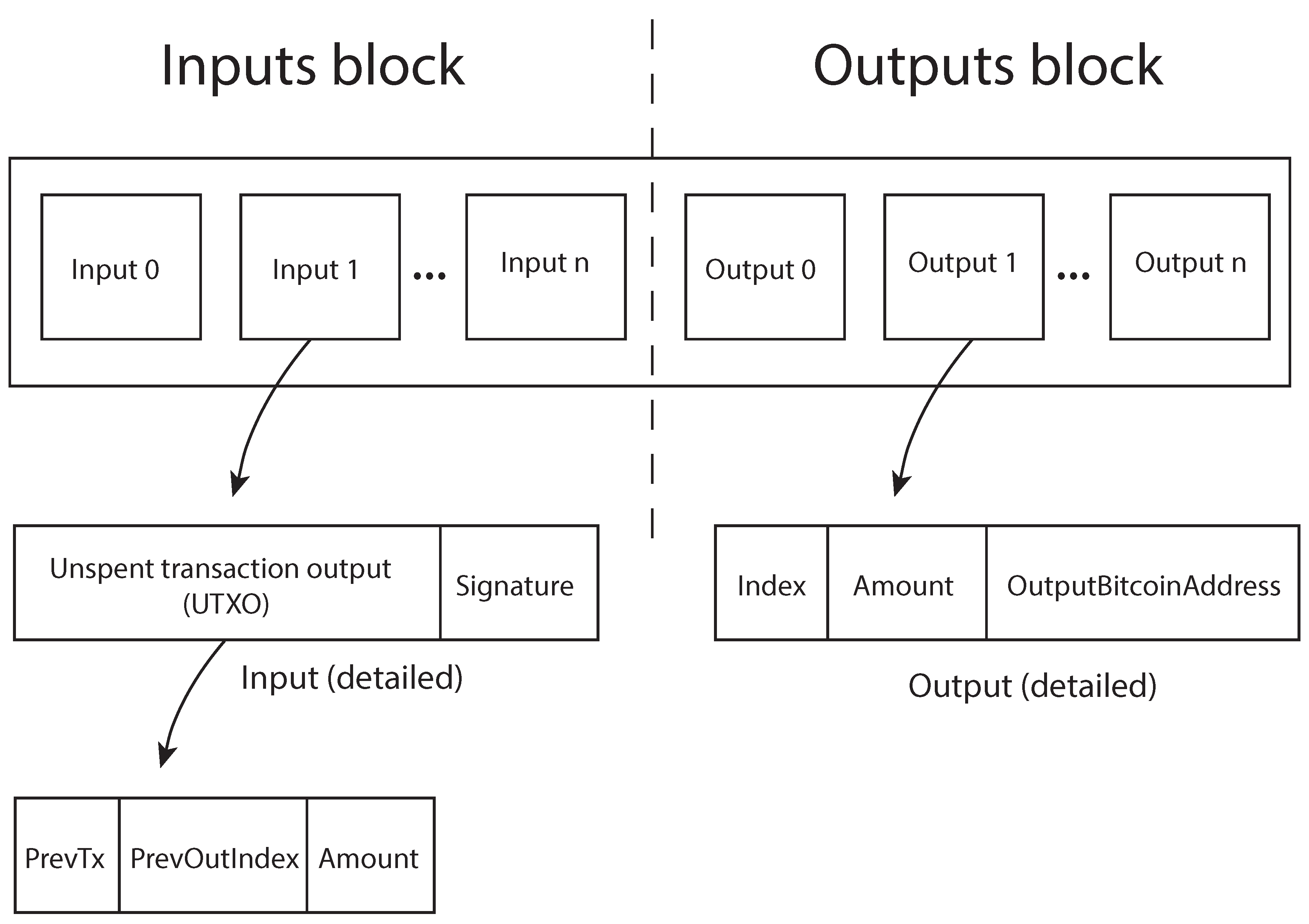
Now, when Alice does some work worth 1 millibitcoinshe asks Bob to create and sign a new version of the refund transaction. Computer network security Reputation management. Views Read Edit View history. However, sometimes the consensus rules are changed to introduce new features or prevent network abuse. Alternatively, proof of work can be used to sybil attack bitcoin mineral Sybil attacks more expensive.

They are not sybil attack bitcoin mineral a general statement of when it is no longer profitable for anyone else. By default, each distinct identity is usually assumed sybil attack bitcoin mineral correspond to a distinct local entity. This page was last edited on 3 Aprilat A local entity may accept a remote identity based on a central authority which ensures a one-to-one correspondence between an identity and an entity and may even provide a reverse lookup. Views Read Edit View history.

Cryptocurrencies work on decentralization sybil attack bitcoin mineral authority and if a few whale miners are sybil attack bitcoin mineral to control the entire consensus mechanism, then cryptocurrencies have lost the very essence of their existence. If the rest of the network is honest, they will reject any invalid transactions coming from the baddie, and they will hear about valid transactions from other honest nodes, even if the miscreant is refusing to pass them on. The vulnerability of blockchains has been a hot topic in the cryptocurrency community recently, especially after the 51 percent attacks on two proof-of-work cryptocurrencies, Electroneum and Verge. Unfortunately it is well known to security researchers that this does not actually increase security; it simply makes the exploits more complicated and difficult to find. They are not making a general statement of when it is no longer profitable for anyone else.
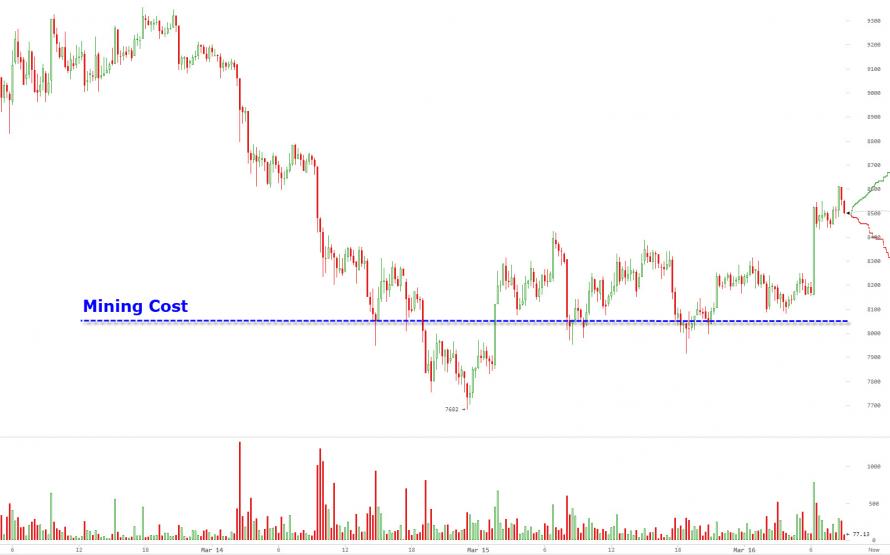
These articles are helping me a lot in understanding bitcoins and blockchain. The vulnerability of blockchains has been a hot topic in the cryptocurrency community recently, especially after the 51 percent attacks on two proof-of-work cryptocurrencies, Electroneum and Verge. Neer Varshney April 12, — sybil attack bitcoin mineral Daily reminder that capital costs of mining dominate ongoing costs.