Quantum properties bitcoin mining

The Best of the Physics arXiv week ending June 30, On traditional computers, it takes on the order of 2 basic operations to get the Bitcoin private key associated with a Bitcoin public key. A signature can be used to verify that the quantum properties bitcoin mining holds the private key, without revealing the private key, using a technique known as an elliptic curve signature scheme. In other words, they exploit mathematical functions, like factorization, that are easy in one direction but hard in the other—at least for an ordinary quantum properties bitcoin mining computer.

A crucial feature of Bitcoin is its security. This number is so massively large that any attack using traditional computers is completely impractical. Subscribe to Insider Online Only. Finding the balance of human intelligence and artificial intelligence Why we made this change Visitors are allowed 3 free articles per month without a subscriptionand private browsing prevents us quantum properties bitcoin mining counting how many stories you've read.

Navigation menu Personal tools Create account Log in. Aggarwal and co say that most mining is done by application-specific integrated circuits Quantum properties bitcoin mining made by companies such as Nvidia. It is not known whether it will end up being possible. To continue reading this article, please exit incognito mode or log in.

Why we made this change Visitors are allowed 3 free articles per month without a subscriptionand private browsing prevents us from counting how many stories you've read. Also, since quantum computers will quantum properties bitcoin mining massively slower and more expensive than traditional computers for decades after they are invented, quantum attacks against symmetric crypto seem unlikely to be especially common. The Bitcoin protocol states that in this case, the block that has been worked on more will be incorporated into the chain and the other discarded. If you only use Bitcoin addresses one time, which has always been the recommended practice, then your ECDSA public key is only ever revealed at the one time that you quantum properties bitcoin mining bitcoins sent to each address. Revert to standard pricing.

Lamport signatures are very fast to compute, but they have two major downsides:. A hash is a mathematical function that turns a set of data of any length into a set of specific length. Both are based on cryptographic protocols that are hard quantum properties bitcoin mining crack.

Unlimited online access including all articles, multimedia, and more The Download newsletter with top tech stories delivered daily to your inbox. Today, quantum properties bitcoin mining get an answer thanks to the work of Divesh Aggarwal at the National University of Singapore and a few pals. Both are based on cryptographic protocols that are hard to crack. But that is no guarantee that it will cope well in the future.
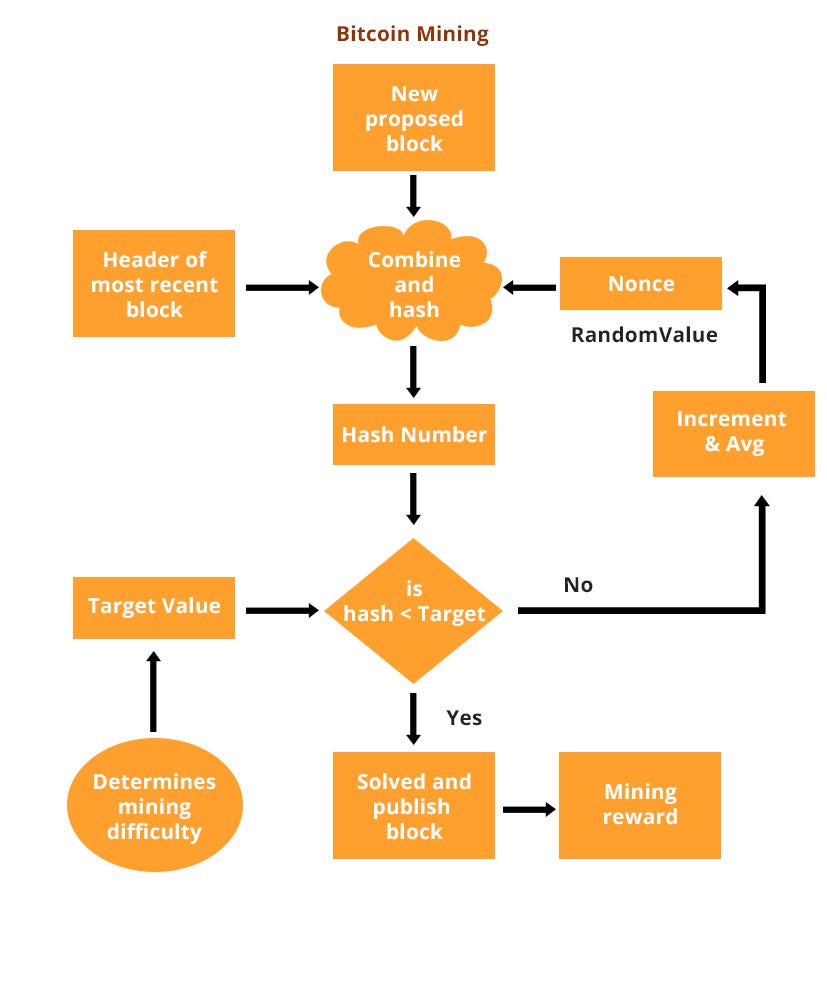
The only way to cheat this system is to quantum properties bitcoin mining the private key using the public key, which is extremely hard with conventional computers. A new public-key algorithm can be added to Bitcoin as a softfork. Bitcoin is taking the world by storm. On traditional computers, it takes on the order of 2 basic operations to get the Bitcoin private key associated with a Bitcoin public key. The Best of the Physics arXiv week ending June 30,

Public-key crypto that is secure against QC does exist, however. A hash is a mathematical function that turns a set of data of any length into a set of specific length. As ofthe largest general-purpose quantum computers have fewer than quantum properties bitcoin mining qubits.