Ethereum tutorial points
The supply of ether on this testnet is also controlled to mitigate spam attacks. A testnet also using proof-of-authority, created by The Ethereum Foundation. Private Ethereum networks allow parties to share data without making it publicly accessible. A private blockchain is a good choice for:. An example of a private enterprise blockchain is Quorum , originally written by J. Read our blog post on using Truffle with Quorum. Applications using smart contracts for their processing are called "distributed applications", or "dapps".
The application itself can be hosted on a traditional web server or on a decentralized file service such as Swarm or IPFS. Given the benefits of the Ethereum blockchain, a dapp could be a solution for many industries, including but not limited to:.
And what is the best way to create your own dapp, test it, and deploy it to an Ethereum network of your choice?
With Truffle , of course. Toggle navigation truffle-logo truffle-logomark. Ethereum Overview You may have heard the terms "blockchain" and "smart contract" floating around, but what do they actually mean? This is a high-level overview covering: Blockchain basics Why use a blockchain? What is a blockchain? How a blockchain works The Ethereum blockchain What is Ethereum?
What is a smart contract? The first databases In the 's the first computerized databases emerged. The need to share data Sharing large amounts of data can be expensive and cumbersome.
Depending on the shared database system, it may feature: Rather than overwriting old data, a new copy is created with the old data retained as a historical record. This record can be accessed to prove a piece of data existed at a certain time.
For a database to be shared, all parties must agree on its contents. There are various methods of reaching consensus, one of which proof-of-work will be discussed below.
Blockchains use these and take them a step further, solving the problem of trust. Blockchains eliminate the problem of trust that affect other databases in the following ways: No single person or group controls a blockchain. Fault tolerance is the ability of a system to handle corrupt data. While fault tolerance is not unique to blockchains, it takes the concept to its logical extreme by having every account sharing the database validate its changes. Transactions can be verified by anyone, without a third party.
This is sometimes referred to as "disintermediation". How a blockchain works Now that we have some idea of why blockchains are useful, let's dive deeper into how they work.
Mining Any node on the network can take part in securing the network through a process called "mining". Hashing Once a new block is mined, the other miners are notified and begin verifying and adding this new block to their copies of the chain. Here's the whole process visually:. Bob attempts to send Alice 1 ETH. Miners compete to validate the block with the new set of transactions.
The victorious miner creates a new block and receives a reward. With the transaction validated, Alice receives 1 ETH. Bob receives Alice's payment along with his collateral. Ethereum networks Up to this point we've been describing the main Ethereum public blockchain or "MainNet". But there are other networks as well. The inherited characteristic "mortal" simply means that the greeter contract can be killed by its owner, to clean up the blockchain and recover funds locked into it when the contract is no longer needed.
Contracts in ethereum are, by default, immortal and have no owner, meaning that once deployed the author has no special privileges anymore. Consider this before deploying. You can get both of these by using a Solidity compiler.
If you have not installed a compiler, you can either:. If you installed the compiler on your machine, you need to compile the contract to acquire the compiled code and Application Binary Interface.
This will create two files, one file containing the compiled code and one file creating the Application Binary Interface in a directory called target. You will see that there are files created for both contracts; but because Greeter includes Mortal you do not need to deploy Mortal to deploy Greeter. You have now compiled your code and made it available to Geth. Now you need to get it ready for deployment, this includes setting some variables up, like what greeting you want to use.
Edit the first line below to something more interesting than "Hello World! If you don't have Solc installed, you can simply use the online IDE. Copy the source code at the top of this page to Remix and it should automatically compile your code. You can safely ignore any yellow warning boxes on the right plane. To access the compiled code, ensure that the dropdown menu on the right pane has greeter selected. Then click on the Details button directly to the right of the dropdown. Create a temporary text file on your computer and paste that code.
Make sure to change the first line to look like the following:. Now you can paste the resulting text on your geth window, or import the file with loadScript "yourFilename.
Wait up to thirty seconds and you'll see a message like this:. You may have to "unlock" the account that is sending the transaction using the password you picked in the beginning, because you need to pay for the gas costs to deploying your contract: There are many useful stats, including the latest gas prices at the network stats page.
Notice that the cost is not paid to the ethereum developers , instead it goes to the Miners , those peers whose computers are working to find new blocks and keep the network secure. Gas price is set by the market of the current supply and demand of computation. If the gas prices are too high, you can become a miner and lower your asking price.
Within less than a minute, you should have a log with the contract address, this means you've successfully deployed your contract. You can verify the deployed code which will be compiled by using this command:. If it returns anything other than "0x" then congratulations!
Your little Greeter is live! The reason is that most of the complications mining, hashing , elliptic-curve cryptography , peer-to-peer networks , etc. A blockchain is a globally shared, transactional database. This means that everyone can read entries in the database just by participating in the network.
If you want to change something in the database, you have to create a so-called transaction which has to be accepted by all others. The word transaction implies that the change you want to make assume you want to change two values at the same time is either not done at all or completely applied. Furthermore, while your transaction is applied to the database, no other transaction can alter it.
As an example, imagine a table that lists the balances of all accounts in an electronic currency. If a transfer from one account to another is requested, the transactional nature of the database ensures that if the amount is subtracted from one account, it is always added to the other account.
If due to whatever reason, adding the amount to the target account is not possible, the source account is also not modified. Furthermore, a transaction is always cryptographically signed by the sender creator. This makes it straightforward to guard access to specific modifications of the database.
In the example of the electronic currency, a simple check ensures that only the person holding the keys to the account can transfer money from it. What happens if two transactions exist in the network that both want to empty an account, a so-called conflict? The abstract answer to this is that you do not have to care. If two transactions contradict each other, the one that ends up being second will be rejected and not become part of the block.
Blocks are added to the chain in rather regular intervals - for Ethereum this is roughly every 17 seconds. The more blocks that are added on top, the less likely it is. So it might be that your transactions are reverted and even removed from the blockchain, but the longer you wait, the less likely it will be. It is not only sandboxed but actually completely isolated, which means that code running inside the EVM has no access to network, filesystem or other processes. Smart contracts even have limited access to other smart contracts.
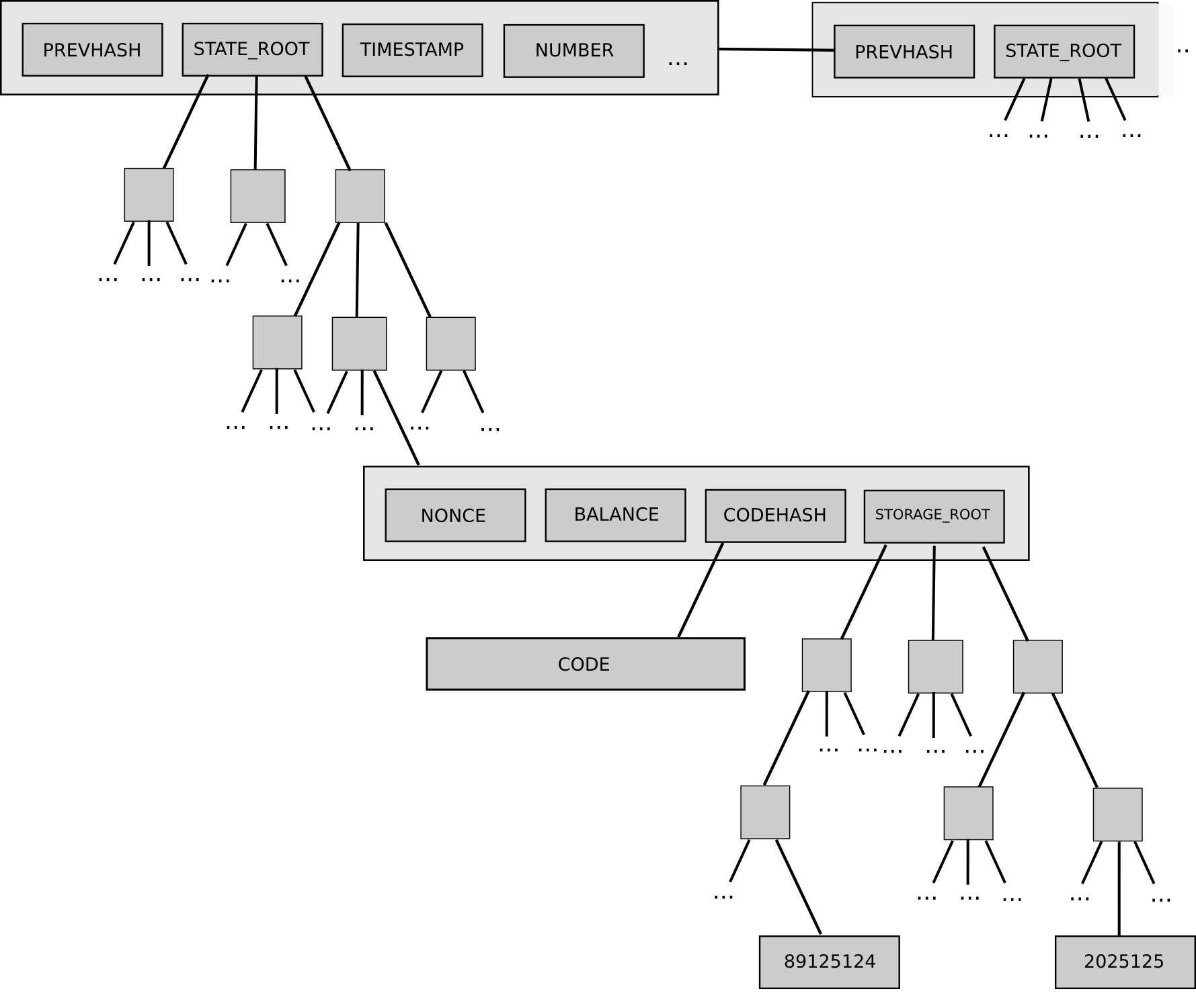
There are two kinds of accounts in Ethereum which share the same address space: External accounts that are controlled by public-private key pairs i. Regardless of whether or not the account stores code, the two types are treated equally by the EVM. Every account has a persistent key-value store mapping bit words to bit words called storage. A transaction is a message that is sent from one account to another account which might be the same or the special zero-account, see below.
It can include binary data its payload and Ether. If the target account contains code, that code is executed and the payload is provided as input data. If the target account is the zero-account the account with the address 0 , the transaction creates a new contract. The payload of such a contract creation transaction is taken to be EVM bytecode and executed.
The output of this execution is permanently stored as the code of the contract. This means that in order to create a contract, you do not send the actual code of the contract, but in fact code that returns that code when executed. While a contract is being created, its code is still empty. Because of that, you should not call back into the contract under construction until its constructor has finished executing.
Upon creation, each transaction is charged with a certain amount of gas , whose purpose is to limit the amount of work that is needed to execute the transaction and to pay for this execution. While the EVM executes the transaction, the gas is gradually depleted according to specific rules.
If some gas is left after the execution, it is refunded in the same way. If the gas is used up at any point i. Each account has a persistent memory area which is called storage. Storage is a key-value store that maps bit words to bit words. It is not possible to enumerate storage from within a contract and it is comparatively costly to read and even more so, to modify storage.
A contract can neither read nor write to any storage apart from its own.